The following is an explanation of Ciso VoIP Extension Mobility (Communications Manager Express) and describes features in Cisco Communications Manager Express (CME) that provide support for phone mobility for end users.
Benefit of Cisco IP Phone Extension Mobility that serve a user login service allows phone users to temporarily access a physical phone other than their own phone and utilize their personal settings, such as directory number, speed-dial lists, and services, as if the phone is their own desk phone. The phone user can make and receive calls on that phone using the same personal directory number as is on their own desk phone.
How to Enable Extension Mobility by perform the following tasks to enable Extension Mobility in Cisco CME:
Before beginning, please note that serious damage can be caused by entering inappropriate commands. Please be careful when altering the configuration of any router.*
1. Set up and associate the physical phone.
The easiest way to avoid searching through lines of configuration or hunting an automatically registered phone is to set up the phone association before plugging it in to a switchport on the network. In other words, give the router a "heads up" that the phone is about to be initialized.
THHQRV1-3845# configure terminal
THHQRV1-3845(config)# ephone 1 #Configuration mode for ephone
THHQRV1-3845(config-ephone)# mac-address 11aa.22bb.33cc #The MAC address for the phone
THHQRV1-3845(config-ephone)# button 1:5 #Assign buttons to the phone by using the ephone-dn
THHQRV1-3845(config-ephone)# type 7962 #Set the phone type
THHQRV1-3845# show ephone ? #Show a list of supported phone types.
2. Create Voice user profile for Extension Mobility
voice logout-profile To enter voice logout-profile configuration mode to create a logout profile and define the default appearance for a Cisco Unified IP phone enabled for Extension Mobility, use the voice logout-profile command in global configuration mode. To delete an logout profile, use the no form of this command:
THHQRV1-3845# configure terminal
THHQRV1-3845(config)# voice logout-profile 1 #Create logout profile
THHQRV1-3845(config-logout-profile)# pin 123456 #Set a PIN to be used by a phone user
THHQRV1-3845(config-logout-profile)# user logout password logout
To configure a user profile for a phone user who logs into a Cisco IP phone that is enabled for Extension Mobility, perform the following steps:
THHQRV1-3845# configure terminal
THHQRV1-3845(config)# voice user-profile 1
THHQRV1-3845(config-user-profile)# user 7222 password 45678
THHQRV1-3845(config-user-profile)# number 7222 type normal
THHQRV1-3845(config-user-profile)# speed-dial 1 90892046844 label "On Call"
3. Creating Directory Numbers
Create an ephone-dn by using the following commands after logging into and enabling your router:
THHQRV1-3845# configure terminal
THHQRV1-3845(config)# ephone-dn 1 dual-line
THHQRV1-3845(config-ephone-dn)# number 7222
THHQRV1-3845(config-ephone-dn)# pickup-group 10
THHQRV1-3845(config-ephone-dn)# description Sumuscha T
THHQRV1-3845(config-ephone-dn)# name Sumuscha Teesr
THHQRV1-3845(config-ephone-dn)# call-forward busy 7111
THHQRV1-3845(config-ephone-dn)# call-forward noan 90811711942 timeout 18
4. Check your running configuration.
You can check your running configuration (ephone-dn, ephone - and other things)
THHQRV1-3845#show running-config
THHQRV1-3845#show run | beg ephone
Download Sample Configurution VoIP Cisco IP Phone CME CUE visio, pdf documents
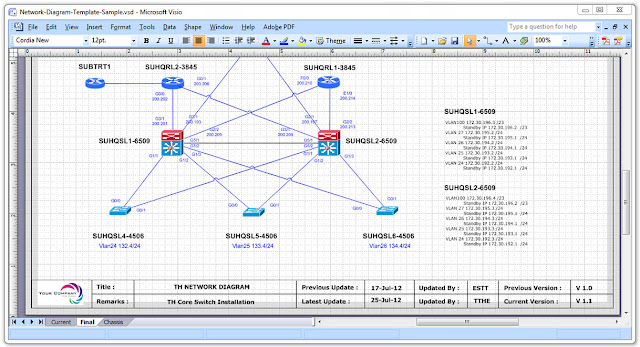
The network topology diagram shows a setup example (Cisco Extension Mobility)
How to Enable Extension Mobility by perform the following tasks to enable Extension Mobility in Cisco CME:
Before beginning, please note that serious damage can be caused by entering inappropriate commands. Please be careful when altering the configuration of any router.*
1. Set up and associate the physical phone.
The easiest way to avoid searching through lines of configuration or hunting an automatically registered phone is to set up the phone association before plugging it in to a switchport on the network. In other words, give the router a "heads up" that the phone is about to be initialized.
THHQRV1-3845# configure terminal
THHQRV1-3845(config)# ephone 1 #Configuration mode for ephone
THHQRV1-3845(config-ephone)# mac-address 11aa.22bb.33cc #The MAC address for the phone
THHQRV1-3845(config-ephone)# button 1:5 #Assign buttons to the phone by using the ephone-dn
THHQRV1-3845(config-ephone)# type 7962 #Set the phone type
THHQRV1-3845# show ephone ? #Show a list of supported phone types.
2. Create Voice user profile for Extension Mobility
voice logout-profile To enter voice logout-profile configuration mode to create a logout profile and define the default appearance for a Cisco Unified IP phone enabled for Extension Mobility, use the voice logout-profile command in global configuration mode. To delete an logout profile, use the no form of this command:
THHQRV1-3845# configure terminal
THHQRV1-3845(config)# voice logout-profile 1 #Create logout profile
THHQRV1-3845(config-logout-profile)# pin 123456 #Set a PIN to be used by a phone user
THHQRV1-3845(config-logout-profile)# user logout password logout
To configure a user profile for a phone user who logs into a Cisco IP phone that is enabled for Extension Mobility, perform the following steps:
THHQRV1-3845# configure terminal
THHQRV1-3845(config)# voice user-profile 1
THHQRV1-3845(config-user-profile)# user 7222 password 45678
THHQRV1-3845(config-user-profile)# number 7222 type normal
THHQRV1-3845(config-user-profile)# speed-dial 1 90892046844 label "On Call"
3. Creating Directory Numbers
Create an ephone-dn by using the following commands after logging into and enabling your router:
THHQRV1-3845# configure terminal
THHQRV1-3845(config)# ephone-dn 1 dual-line
THHQRV1-3845(config-ephone-dn)# number 7222
THHQRV1-3845(config-ephone-dn)# pickup-group 10
THHQRV1-3845(config-ephone-dn)# description Sumuscha T
THHQRV1-3845(config-ephone-dn)# name Sumuscha Teesr
THHQRV1-3845(config-ephone-dn)# call-forward busy 7111
THHQRV1-3845(config-ephone-dn)# call-forward noan 90811711942 timeout 18
4. Check your running configuration.
You can check your running configuration (ephone-dn, ephone - and other things)
THHQRV1-3845#show running-config
THHQRV1-3845#show run | beg ephone